Proxy Automation
Introduction to Proxy Automation
Proxy automation has become essential for businesses that need to manage network traffic at scale. By programmatically controlling proxy servers, organizations can rotate IP addresses on the fly, manage authentication, and detect failures in real time—without any manual intervention. Unlike traditional proxy setups, automated systems distribute requests across large proxy pools and adapt their configurations based on current network conditions. At GeeLark, we’ve built proxy automation directly into our cloud phone platform to unify device fingerprint management and network identity control in a single, streamlined solution.
Understanding Proxy Servers: Types and Applications
Types of Proxies
Residential proxies use genuine ISP-assigned IP addresses that appear to come from ordinary home users. Some providers maintain vast networks—offering access to more than 55 million unique residential IPs.
- Datacenter Proxies: High-speed proxies (often <0.3 s response times) hosted in data centers, which may be more detectable.
- Mobile Proxies: Cell-network IPs for mobile-specific tasks. Providers such as Proxyma offer solutions tailored for mobile use cases.
- SOCKS5 Proxies: Support multiple traffic types (TCP, UDP) and are versatile for diverse applications.
Key Applications
Effortlessly manage multiple social media or e-commerce accounts without triggering security alerts. By leveraging GeeLark’s cloud phone solution, you can significantly reduce the risk of account bans.
- Web Scraping: Enable large-scale data collection while avoiding IP-based blocks.
- Ad Verification: Test ad placements from various geographic locations.
- Market Research: Collect competitive intelligence across regions.
Core Components of Proxy Automation
- Intelligent Rotation Engine: Chooses proxies based on target site behavior rather than simple cycling.
- Health Monitoring System: Tracks metrics like success rate and response time.
- Failover Mechanisms: Redirect traffic away from failing proxies.
- Traffic Shaping: Mimics human request patterns to avoid detection.
- Configuration Management: Centralizes proxy settings across all devices or sessions.
GeeLark augments these components with integrated identity profiles, binding proxy settings at the device level for each cloud phone instance.
Benefits of Automating Proxy Management
- Operational Continuity: In a six-month internal test, automatic failover maintained connections with a 99.47% success rate across blocked proxies.
- Cost Optimization: One client reported a 40% reduction in proxy expenses after adopting automation.
- Improved Success Rates: Intelligent rotation boosted data collection success from 65% to 92%. For example, Company X reduced CAPTCHA challenges by 50% after deploying our rotation engine.
- Scalability: Support thousands of concurrent sessions without proportional overhead.
- Time Savings: Eliminates hours of manual configuration and troubleshooting.
Implementing Proxy Automation in Cloud Environments
Native Proxy Integration
GeeLark Cloud Phone supports HTTP, HTTPS, and SOCKS5 proxies at the system level so that all apps and browsers inherit the correct settings automatically.
- Region auto-matching based on proxy location
- Custom proxy configurations for specialized workflows
- Persistent proxy settings across sessions
Geographic Flexibility
By pairing GeeLark cloud phones with location-specific proxies, organizations can:
- Simulate user presence in any supported region
- Test region-locked content and services
- Manage geo-targeted accounts with proper digital footprints
Implementation Examples
API-Driven Control
# Configure a SOCKS5 proxy for a cloud phone
response = requests.post(
'https://api.geelark.com/v1/devices/proxy',
headers={'Authorization': 'Bearer YOUR_API_KEY'},
json={
'device_id': 'CLOUD_PHONE_ID', # Target cloud phone
'proxy_type': 'socks5', # Proxy protocol
'host': 'proxy.example.com', # Proxy server address
'port': 1080, # Proxy port number
'credentials': {
'username': 'user123', # Proxy username
'password': 'securepass' # Proxy password
}
}
)
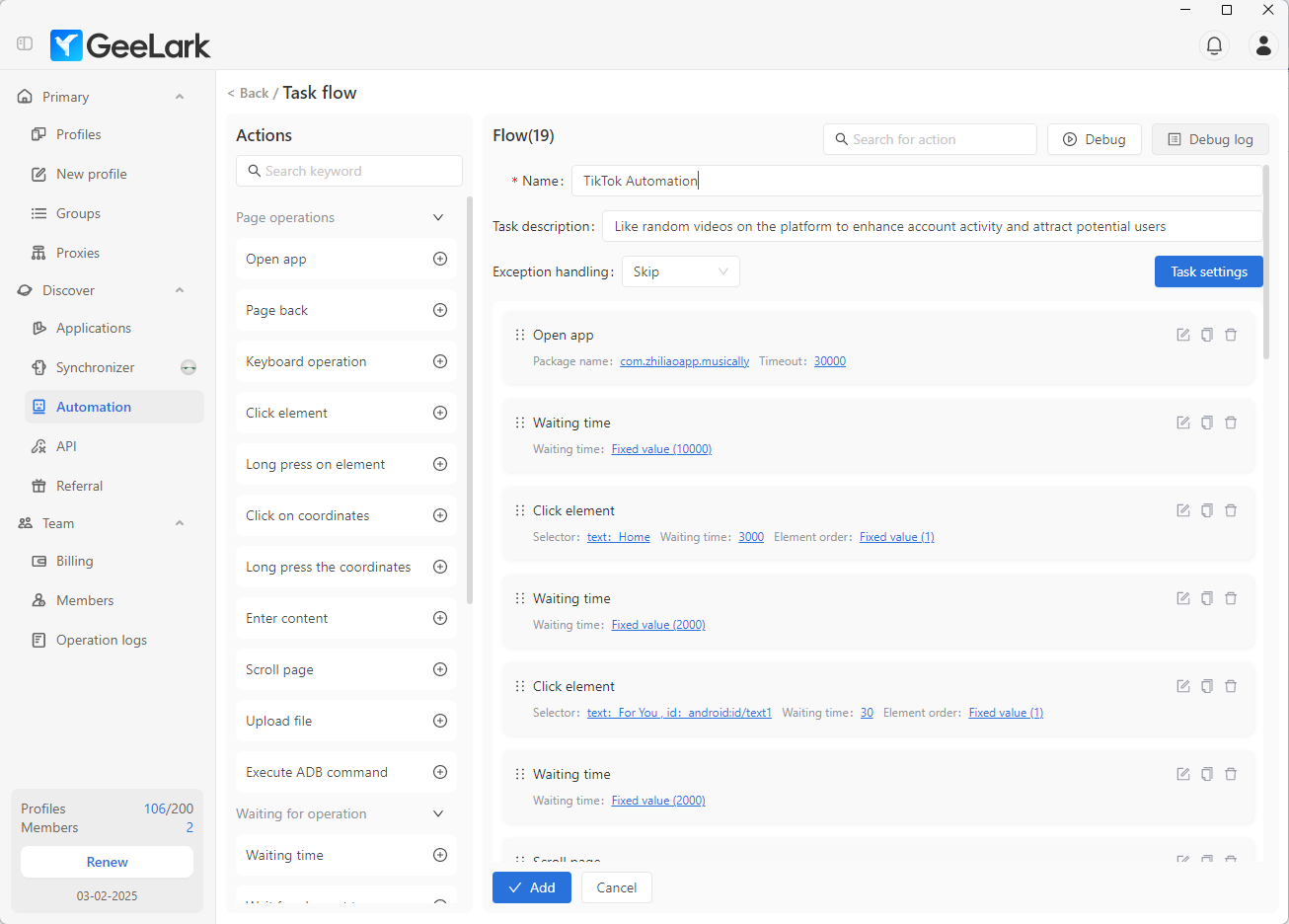
Visual (Low-Code) Automation
- Drag-and-drop workflow builder
- Pre-configured proxy rotation templates
- Scheduled IP rotation and health checks
Best Practices for Proxy Automation
- Diversify Proxy Sources: Mix residential, datacenter, and mobile proxies.
- Implement Intelligent Rotation: Use unpredictable patterns to avoid detection.
- Monitor Key Metrics: Track success rates, response times, and error trends.
- Respect Target Sites: Follow robots.txt and limit request rates.
- Secure Proxy Credentials: Use authentication and encrypt sensitive data.
Future Trends in Proxy Automation
- AI-Optimized Routing: Machine learning selects the best proxy based on real-time site responses, reducing failed requests.
- Integrated Identity Management: Unified control of device fingerprints and network identities to prevent cross-session leaks.
- Decentralized Proxy Networks: Peer-to-peer systems offering resilience against large-scale bans.
- Advanced Mobile Emulation: Tighter integration with cellular networks to improve mobile-specific testing and scraping.
Conclusion
Proxy automation has evolved into a core requirement for scalable digital operations. By programmatically managing proxies, businesses can focus on strategic initiatives rather than network maintenance. The cloud phone platform from GeeLark uniquely blends automated proxy management with device identity control for end-to-end scalability, security, and reliability.
People Also Ask
What does an auto proxy do?
An auto proxy automatically assigns and rotates proxy IP addresses across requests or sessions. It detects and replaces failed or blocked proxies in real time, manages authentication, and balances traffic to avoid rate limits. By eliminating manual configuration, it ensures continuous anonymity, load distribution, and uninterrupted access.
What are the three types of proxies?
The three basic proxy types by anonymity level are:
- Transparent Proxy – forwards your IP and flags itself as a proxy, often used for caching or content filtering.
- Anonymous Proxy – hides your IP but still identifies as a proxy to the destination.
- Elite (High-Anonymity) Proxy – conceals both your IP and the fact you’re using a proxy, offering the strongest privacy.
Should automatic proxy setup be on or off?
Automatic proxy setup is best enabled when you’re on a network that provides a central configuration (via WPAD or a PAC file), such as in corporate or campus environments—this ensures you always use the correct proxy without manual tweaks. On home or public networks that don’t require a proxy, leave it off to avoid unnecessary routing delays or connection errors. If you encounter slow or blocked access, switch off automatic setup and connect directly or configure a specific proxy manually.
Is a proxy server illegal?
Proxy servers aren’t illegal per se. They’re legitimate networking tools used for caching, load balancing, privacy, and security. However, using proxies to commit illegal activities like hacking, piracy, fraud, or bypassing geo-restrictions can be unlawful. Some countries also restrict or block proxy use, so always check local regulations and use them responsibly.







