Proxy Integration
Introduction
Proxy integration is a critical component in modern cloud services, especially for platforms managing multiple digital identities. At GeeLark, our cloud phone solution delivers hardware-based Android environments that include genuine device fingerprints—far beyond what antidetect browsers can simulate. Each GeeLark instance runs on real hardware, so your network traffic appears indistinguishable from a physical device’s.
Understanding Proxy Integration
Proxy integration in GeeLark securely routes each cloud phone’s network traffic through designated servers, ensuring complete isolation, geographic authenticity, and policy enforcement. Proxies act as intermediaries that forward requests and responses, masking original IPs and centralizing control.
Key proxy types:
- HTTP/HTTPS: Optimized for web browsing and scraping
- SOCKS5: Supports all TCP/UDP traffic for advanced apps
- Residential: Uses ISP-issued IPs, hardest to detect
Core functions in cloud environments:
- Access control: Allow or block traffic by rule
- Traffic routing: Direct requests through chosen network paths
- Request modification: Alter headers and metadata for anonymity
- Authentication: Verify credentials before granting access
Anonymity levels:
- Transparent proxies: IP exposed, easy to detect
- Anonymous proxies: IP hidden, moderate detection risk
- High-anonymity proxies: IP hidden, very hard to detect
The Technical Foundation of Proxy Integration
GeeLark’s network layer leverages standard protocols and robust architecture to deliver secure, high-performance proxy integration.
Network protocols:
- HTTP CONNECT: Creates encrypted tunnels for HTTPS
- SOCKS5: Routes arbitrary traffic types
- TLS handshakes: Ensure secure data transmission
Proxy server architecture:
- Frontend listener: Receives client connections
- Authentication layer: Validates user credentials
- Routing engine: Selects exit nodes
- Logging system: Records connection metadata and performance
Supported authentication:
- IP whitelisting (no credentials)
- Username/password
- Signature-based for API-driven workflows
GeeLark’s Proxy Integration Capabilities
GeeLark’s enterprise-grade proxy management empowers you to:
- Centralize all proxy configurations in one dashboard
- Perform bulk operations across hundreds of cloud phones
- Leverage a full REST API for automation
- Monitor usage analytics and performance metrics
Supported proxy types:
- HTTP/HTTPS (ports 80, 8080, 443)
- SOCKS4/SOCKS5 (ports 1080, 1081)
- Residential proxies with automatic rotation
- Dedicated datacenter proxies
Per-device configuration lets you assign:
- Unique proxy settings
- Custom authentication credentials
- Location-specific exit nodes
- Protocol-specific parameters
API Access Example
Automate proxy assignment with GeeLark’s REST API:
curl -X POST https://api.geelark.com/v1/devices/{device_id}/proxy \
-H "Authorization: Bearer YOUR_API_TOKEN" \
-H "Content-Type: application/json" \
-d '{
"host": "proxy.geelark.com",
"port": 1080,
"protocol": "socks5",
"username": "user123",
"password": "pass123"
}'Setting Up Proxies in GeeLark
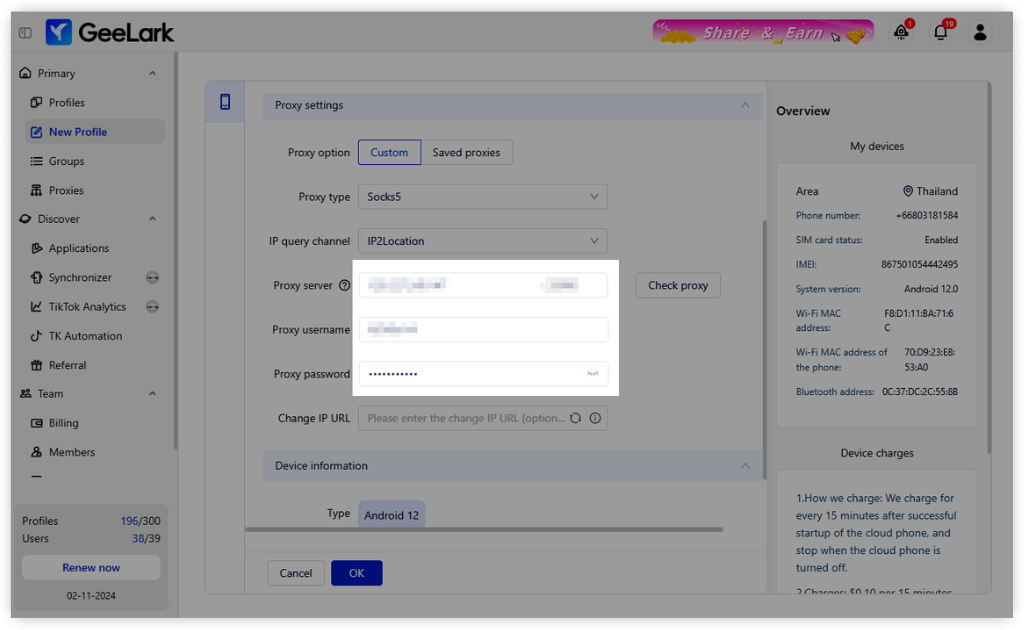
Follow these steps to configure proxies on your cloud phones:
- Navigate to the Proxy Management section in the GeeLark dashboard.
- Click Add New Proxy and enter server details (IP, port, protocol).
- Provide authentication credentials if required.
- Click Test Connection to verify latency and anonymity.
- Assign the configured proxy to one or multiple cloud phones.
Benefits of Proxy Integration with GeeLark
Enhanced Privacy and Security
- Complete IP masking through encrypted tunnels
- No direct exposure of your cloud phone to target services
- Protection against IP-based tracking and fingerprint linking
IP Diversification for Multi-Account Management
- Hundreds of unique IP addresses with automatic rotation
- Geographic distribution aligned with your use case
- Sticky sessions when required for longer workflows
Bypassing Geographical Restrictions
- Access region-locked content via target-country proxies
- Mimic local user behavior to avoid VPN detection
- Maintain consistent geo-identity across sessions
Preventing Account Associations
- Hardware-level device IDs prevent emulator detection
- Isolated network tunnels avoid IP and cookie linkages
- Complete Android environments eliminate fingerprint correlation
Best Practices for Proxy Integration
Selecting proxy types by use case:
- Social media: Residential proxies
- E-commerce: Dedicated datacenter proxies
- Market research: Geo-targeted residential proxies
- Security testing: Rotating SOCKS5 proxies
Performance optimization:
- Choose proxies geographically close to your targets
- Monitor and replace underperforming proxies regularly
- Balance load across multiple providers
- Implement intelligent rotation policies
Security considerations:
- Never reuse credentials across proxies
- Audit proxy access logs frequently
- Apply IP whitelisting where possible
- Always use encrypted protocols (HTTPS/SOCKS5)
Conclusion
Proxy integration is the backbone of effective cloud phone management, and GeeLark sets a new industry standard with hardware-based Android environments and advanced network controls. Unlike emulators or antidetect browsers, GeeLark delivers:
- Authentic device fingerprints from real hardware
- Complete Android OS environments for app execution
- Enterprise-grade proxy management at scale
- Unmatched automation via REST APIs
Sign up and start your first cloud phone instance and stay ahead of detection algorithms and operate securely at any scale with GeeLark.
People Also Ask
How to integrate proxy?
- Obtain your proxy details (IP, port, protocol, username/password).
- For system-wide use, set environment variables:
• HTTP_PROXY=http://user:pass@proxy_ip:port
• HTTPS_PROXY=https://user:pass@proxy_ip:port - In a browser, enter the proxy in network or connection settings.
- In code or CLI tools, configure the HTTP client library or tool flags to point to your proxy address and credentials.
- Verify the integration by accessing a site like “whatismyip” and confirming the displayed IP matches your proxy.
What is proxy integration in API gateway?
Proxy integration in an API Gateway is an integration mode where the gateway acts as a transparent reverse proxy, forwarding incoming requests—method, path, headers, query strings, and body—directly to a backend endpoint (HTTP service or Lambda) with minimal transformation. Responses from the backend are passed back unchanged to the client. This “pass-through” approach simplifies configuration by eliminating the need for explicit mapping templates or resource definitions for each parameter.
What is a proxy vs API?
A proxy is an intermediary that routes HTTP(S) traffic between clients and servers, handling tasks like caching, access control, or anonymity at the network layer. An API (Application Programming Interface) is a set of software-defined endpoints, methods, and message formats that enable applications to interact and exchange data at the application layer. A proxy passes through and possibly transforms raw requests, whereas an API specifies the exact functions and data structures available to clients.
What is the primary purpose of proxy integration in API integration?
Proxy integration lets an API gateway act as a transparent pass‐through between clients and backend services. Its primary purpose is to forward incoming HTTP requests—including paths, headers, query strings, and bodies—directly to the target endpoint (HTTP service or Lambda) with minimal setup. This simplifies API configuration by eliminating custom mapping templates and resource definitions, speeds up development, and ensures all request and response data flows unchanged, while still allowing you to apply gateway‐level controls like authentication, throttling, and logging.







